Automating Domain Squatting Detection with DNSTwist and Python
There’s a good chance that, at some point, you’ve received a
spam email with a link that looked close to the name of a popular domain but was
just a little off. Payapl.com instead of Paypal.com or similar.
Domain squatting is a malicious activity where attackers
register domain names similar to legitimate ones. Attackers may use these
domains to deceive users into believing they are visiting a legitimate website,
which can lead to phishing and other attacks.
DNSTwist (available here: https://github.com/elceef/dnstwist)
is a popular tool that helps identify domain names that are similar to a given
domain name. It generates a list of potential domain names by applying various
fuzzing techniques to the given domain name and then checks if these domains
are registered.
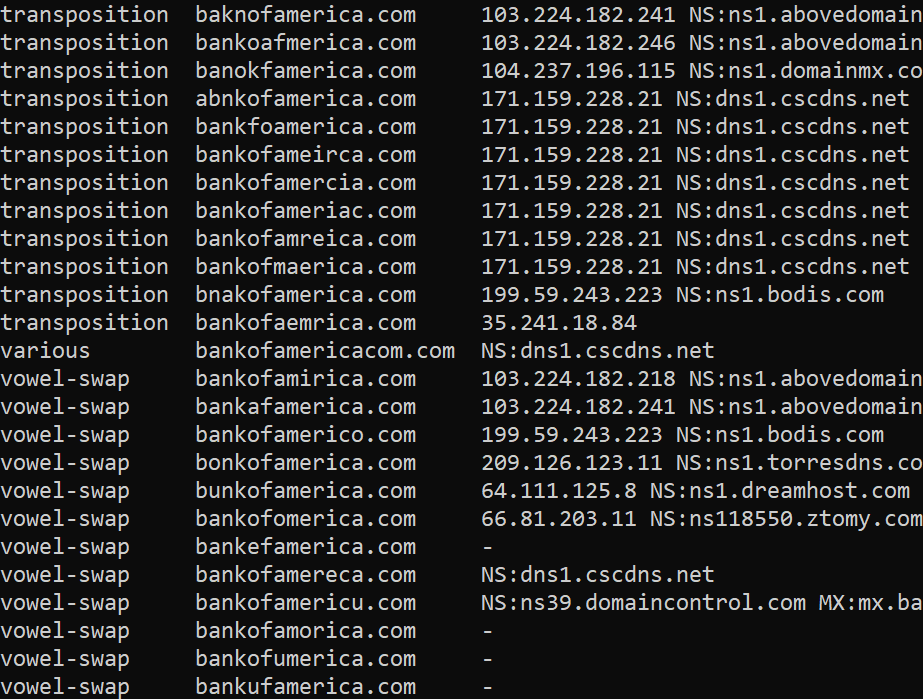
Check out the list of Bank Of America copycat domains:
DNSTwist is an amazing tool that should likely be a part of
every organization's Cyber Threat Intelligence monitoring efforts, and I wanted
to automate it slightly. My goal was to write a short Python script I could run
once a day which would:
- 1. Run DNSTwist and save a list of the registered domains to a JSON file
- 2. Compare the results to the previous results when that domain was checked
- 3. Fire an alert if a new domain is found
The code is available at: https://github.com/ArgeliusLabs/dnstwist_diff
The script will run for each domain in the DOMAINS list near
the beginning of the code. Currently, the alert is printed to the screen and
sent to a Slack Webhook, but that can be commented out or modified. There is
also a delay built in between domains checked in case you’re checking a large
number of domains and don’t want to overwhelm your DNS server.
The code is fairly straightforward and easily modifiable to
your custom needs. If you do make any custom mods, I would love to hear about
them!

Comments
Post a Comment